Amsterdam, 28 January 2026 — Organizations are structurally unprepared for the expected wave of AI-driven cyberattacks in 2026. This is revealed by recent research from international cybersecurity company Hadrian. Two out of three CISOs and security experts identify AI-driven threats as their top concern for 2026. Compounding the problem, 99.5% of the findings security teams deal with are false positives.
With only 0.47% of the security issues actually exploitable, security professionals are spending more time sorting through tickets than fixing issues. As a result, cyber threats are increasingly exposed, often without security teams knowing they exist.
“Traditional defensive cybersecurity will no longer be sufficient in an AI-first world in 2026,” says Rogier Fischer, CEO of Hadrian. “The only viable path forward is a decisive shift toward continuous, offensive cybersecurity, powered by automation and real-world exploit validation.”
Cybersecurity at a breaking point
Hadrian’s 2026 Offensive Security Benchmark Report reveals an industry at a breaking point: security teams are overwhelmed by alerts, blind to AI-driven attack surfaces, and increasingly outpaced by adversaries who already operate at machine speed. Nearly 90% of all verified exposures are rated medium or low severity, creating alert fatigue that obscures the small fraction of issues that are truly exploitable. Critical exposures represent just 3% of validated findings, yet are buried among thousands of competing alerts.
Fischer adds: “The biggest risk going into 2026 isn’t that organizations lack security tools. It’s that they no longer know which threats are real while attackers know exactly where to strike.”
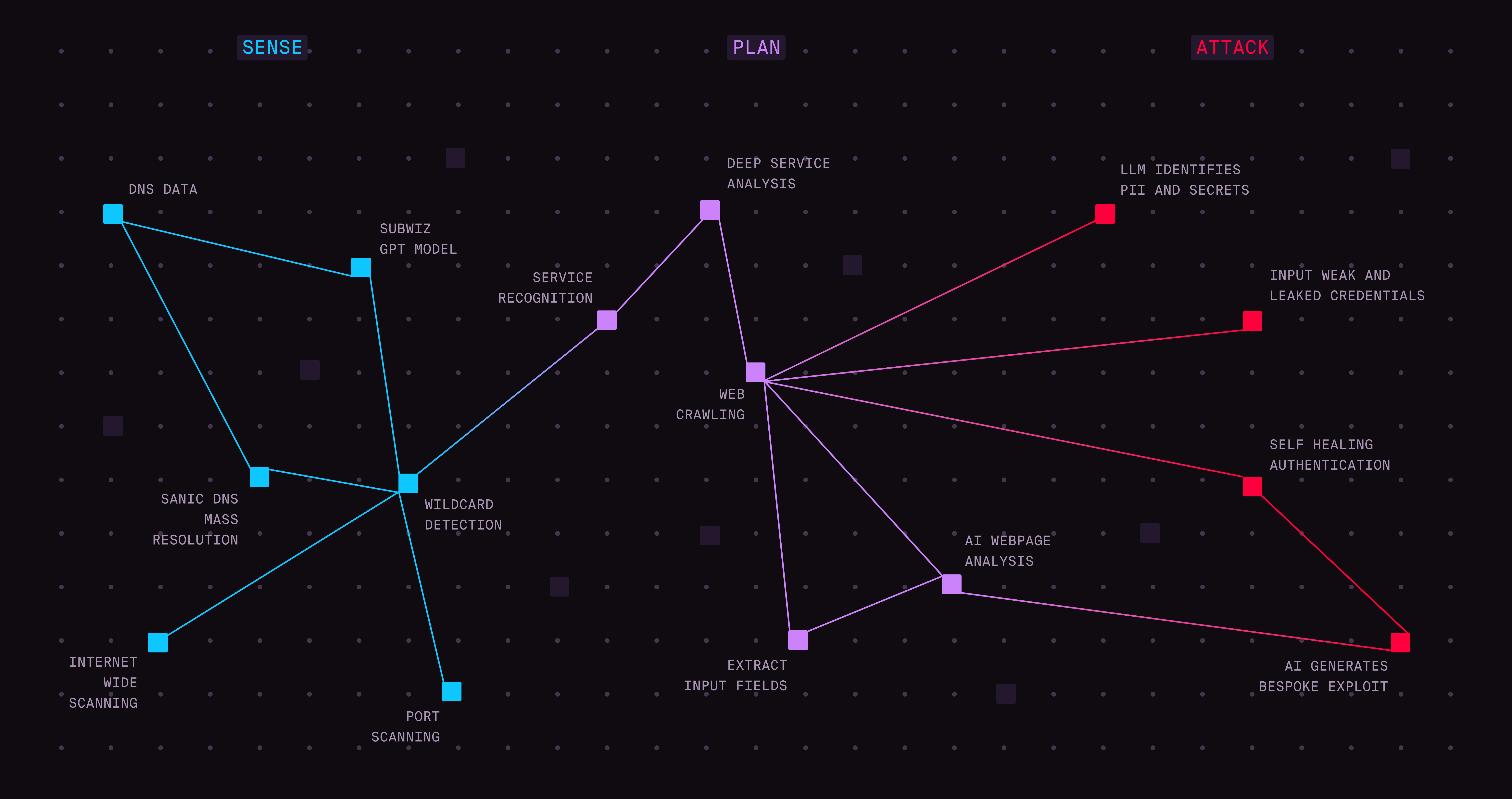
AI has permanently shifted the balance of power in cybersecurity. Attackers now weaponize automation, large language models and AI-assisted reconnaissance to discover, exploit and chain vulnerabilities within hours. Defenders, by contrast, remain stuck manually validating alerts and debating priorities.
Measurable impact
The impact is measurable. Critical vulnerabilities take an average of 4 days to remediate, with some remaining open for more than four months, but exploitation often begins in hours. When urgency is undeniable, speed is possible: 94% of zero-day vulnerabilities are remediated within five days. The gap is not technical capability, but certainty.
Offensive security becomes mandatory
The report reaches one unavoidable conclusion: organizations can only defend at the speed at which they can validate reality. Attackers already think offensively. They test, chain, and exploit continuously.
In 2026, defenders must do the same by adopting automation, adversarial emulation and continuous exploit validation to identify what truly matters before it is weaponized. This is not a tooling upgrade. It is a strategic shift in mindset: from compliance to confrontation and from defense to verified dominance of the attack surface. For executive teams, the message is clear: if you cannot validate what is exploitable today, you will not be able to prevent breaches tomorrow.
“The industry has treated offensive cybersecurity as something advanced or optional for too long,” says Fischer. “It should be the baseline. If you’re not continuously testing your environment the way attackers do, you’re no longer defending, you’re guessing.”
Note to editors:
Methodology
The 2026 Offensive Security Benchmark Report is based on a combination of verified risk data collected throughout the 2025 calendar year and quantitative survey research:
- Verified risk data from 300+ organizations across the US, UK, Netherlands, Germany, France and Italy.
- Continuous real-world exploitation by Hadrian’s ethical hackers.
- Quantitative analysis of attack surfaces, exploitability and remediation timelines.
- A focus group of 34 enterprise CISOs and senior SecOps leaders across multiple industries.
- Cross-validation between platform telemetry, attacker behavior, and executive insights.
About Hadrian
Hadrian is a leading cybersecurity company specializing in offensive security solutions. With the mission to empower organizations from a hacker’s perspective, Hadrian uses advanced technologies to identify and mitigate vulnerabilities before they can be exploited. Through continuous monitoring and proactive threat analysis, Hadrian supports companies worldwide in building resilient digital infrastructures in an increasingly complex cyber landscape.