
Sense
Automating reconnaissance with hacker intuition
Start where the hackers start
Hadrian's offensive security platform starts where the attacker starts: the internet. The root cause of breaches has tripled in the last 2 years.
Hadrian performs continuous discovery, with scans typically running on an hourly basis or after an event-based trigger to maintain a complete inventory of the addressable scope.
Our discovery methods include traditional methods:
- non-invasive passive scans that continually monitor the IPv4 space
- DNS changes
- WHOIS records
- and certificate transparency logs to identify new domains.
These are enriched by our AI agents, such as Subwiz, that can predict forgotten subdomains, expanding the known attack surface by 20-50% alone.

Agentisches Testing ersetzt Pentests
A successful Sense phase must eliminate blind spots by identifying assets that have bypassed formal IT processes. Hadrian uses a proprietary holistic approach to asset attribution by building an asset profile for the organization.
We leverage Machine Learning to confirm asset ownership by analyzing 32 categories of factors of the known attack surface and then scanning the internet for assets that match the profile.
This includes both technical (code fingerprinting) and non-technical (logos, brand colors) to identify Shadow IT. Hadrian provides enhanced visibility into edge and IoT devices as well as third-party SaaS applications.
These far-reaching discovery mechanics ensure you are not compromised by forgotten or shadow assets that pose an out-of-scope risk.
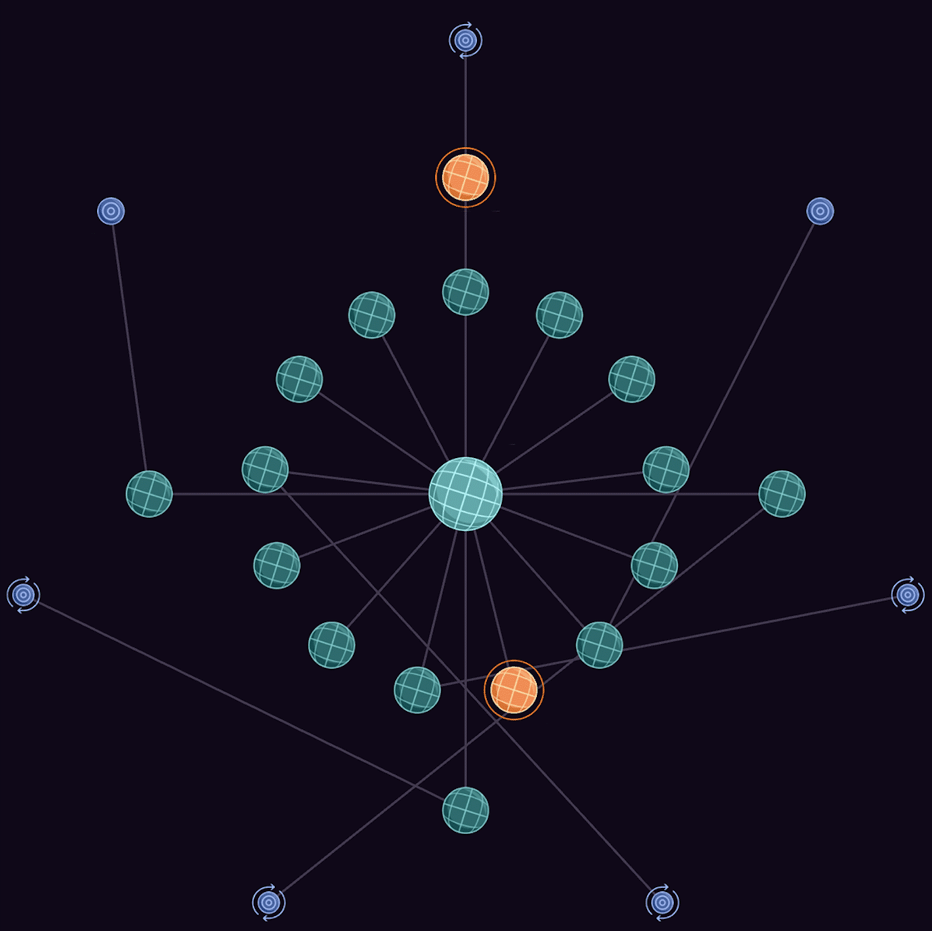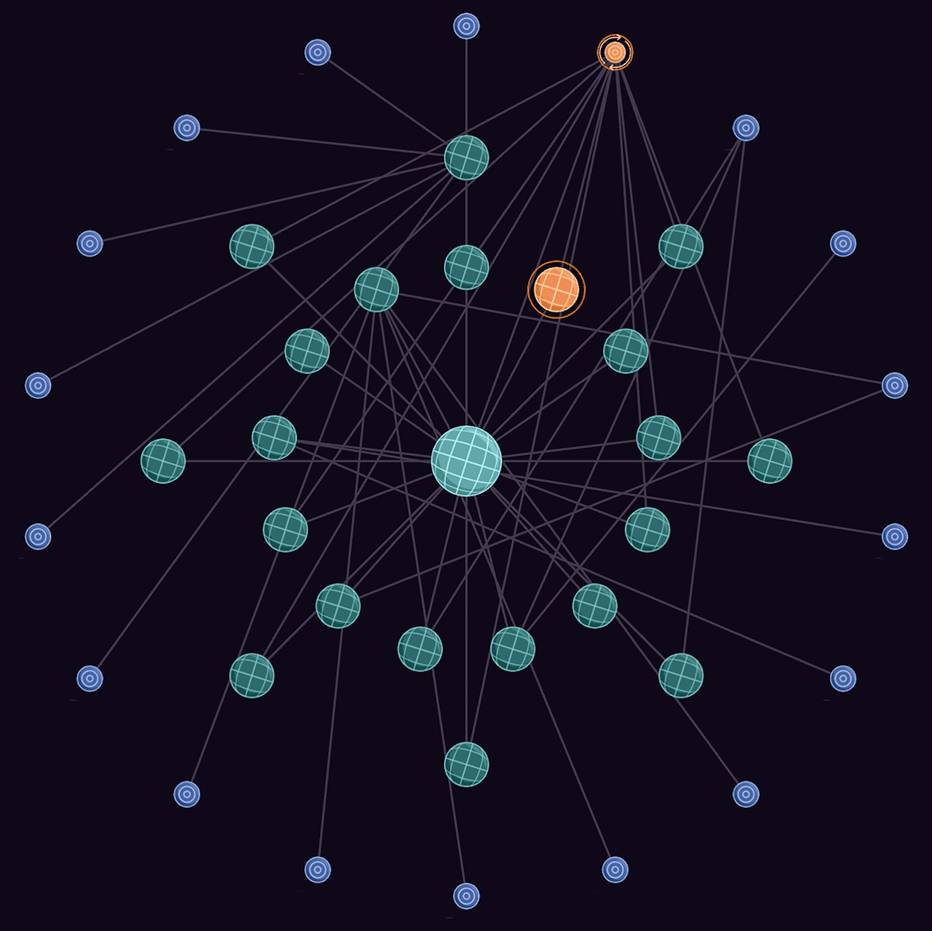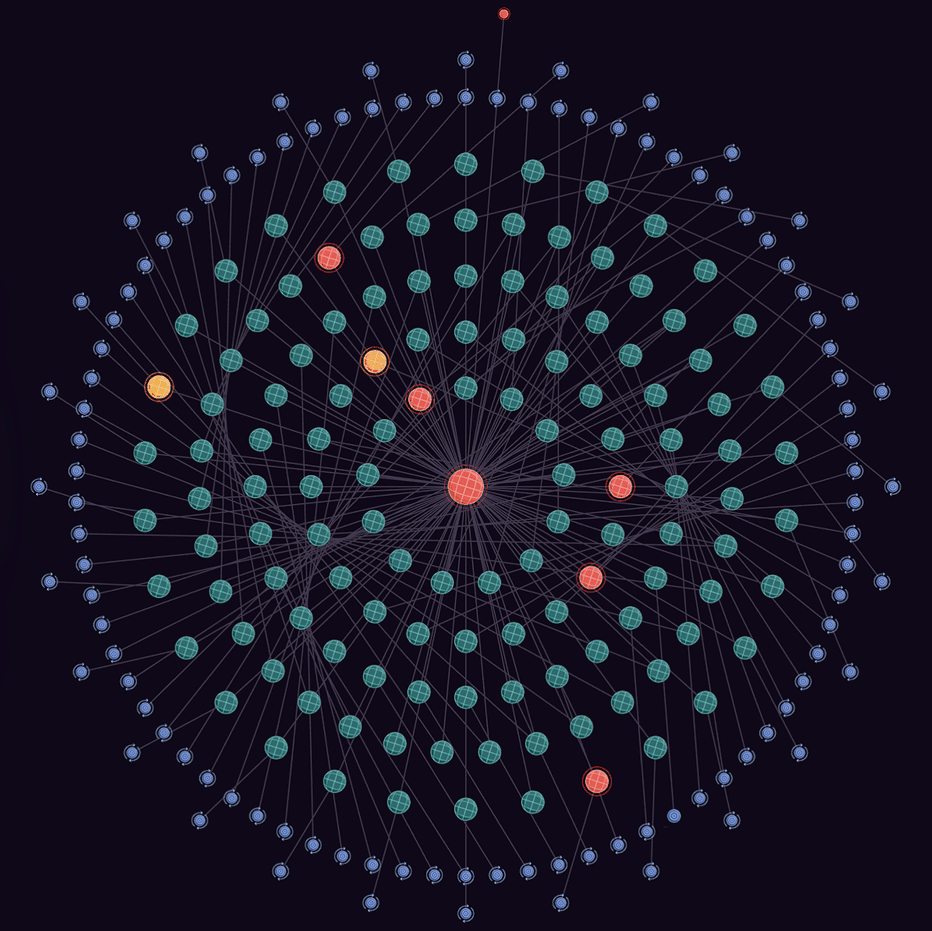
Holistic, far-reaching asset context mapping
Hadrian’s Sense phase transforms raw discovery data into security intelligence by building deep context and visualizing interconnections. This includes direct, cloud-native integrations with AWS, GCP, and Azure, with the inventory refreshed on the hour, every hour.
The continuous correlation of assets is displayed in Hadrian’s Asset Graph visualization, helping analysts see interconnection and understand the blast radius of a potential attack path.
Crucially, Hadrian uses machine learning to find look-alike domains used in phishing attacks that could harm your brand’s reputation and customers. In addition to that, Hadrian performs dark web monitoring for stolen credentials via malware infection on an edge device within a network.
Take the first step in the shoes of your adversary
Hadrian provides you with the hacker’s perspective on your internet-facing business to fortify your cybersecurity posture. Curious to know what they see?
Branchenführend
Hadrian wurde das zweite Jahr in Folge im GigaOM Radar Report for Attack Surface Management als Leader ausgezeichnet und erhielt den New Product Innovation Award for External Attack Surface Management von Frost & Sullivan.


