


Detect Infostealers Infections
Know when data from your business appears on the dark web such as login credentials and even session tokens.

Seal yourself off from infostealer leaks
Infostealers infections are a particularly dangerous type of malware that can siphon off sensitive data and sell it to the highest bidder on the dark web. Hadrian ethically monitors dark web activity and can detect if your organization’s data is being traded illegally.
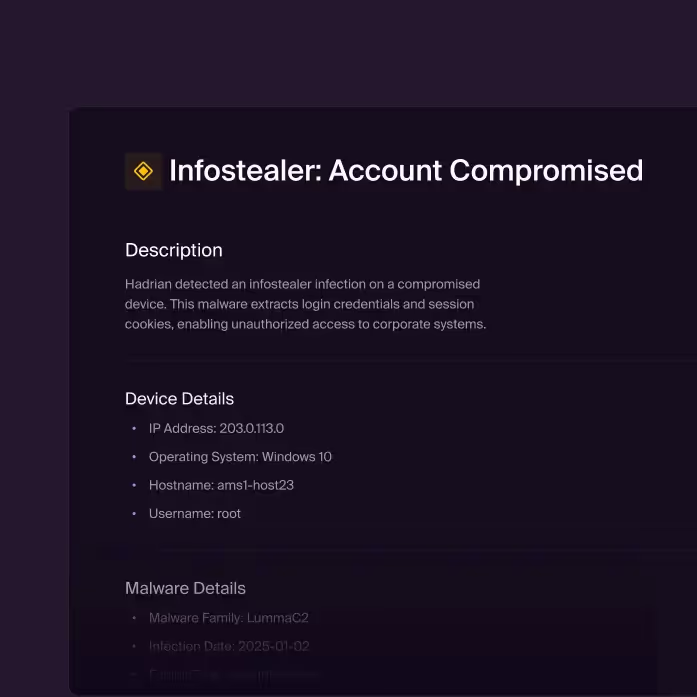
Prevent unauthorized access from stolen data
Review all information about an Infostealers attack affecting your organization including the identification of the infected device, infostealer malware type, compromised accounts, and stolen session cookies, along with clear guidance to help you contain the threat quickly.

Review compromised credentials and remediate
In addition to infostealer infections, you can view all of the compromised credentials associated with your organization. The credentials include those tied to your organization’s corporate email addresses or login service on your domains. Each entry shows the username, a partially masked password, target URL, source type, and post date.

























Latest resources.
All resourcesTake the first step in the shoes of your adversary
Hadrian provides you with the hacker’s perspective on your internet-facing business to fortify your cybersecurity posture. Curious to know what they see?






.png)