


Adversarial Exposure Validation
Pinpoints the exposures that can actually be exploited in real-time with continuous emulation of real‑world attackers from the outside‑in.

Real-time testing of every asset. 24/7.
Hadrian’s cloud platform runs 24/7 reconnaissance and mimics hacker penetration testing the moment your attack surface changes. Whether it’s a misconfiguration, shadow asset, or the latest zero-day, AEV finds it fast and provides clear proof-of-exploit steps. Continuous, event‑driven scanning ensures nothing slips through the cracks, giving you round‑the‑clock protection against the threats that matter most.

Threat validation that keeps you focused
Tired of sifting through thousands of meaningless alerts? AEV delivers only what’s provably exploitable. By chaining real attack paths and providing step‑by‑step proof‑of‑exploit, it slashes false positives to zero and cuts alert volume. Your team focuses on a concise, prioritized list of true risks that can help you accelerate remediation by up to 80%.
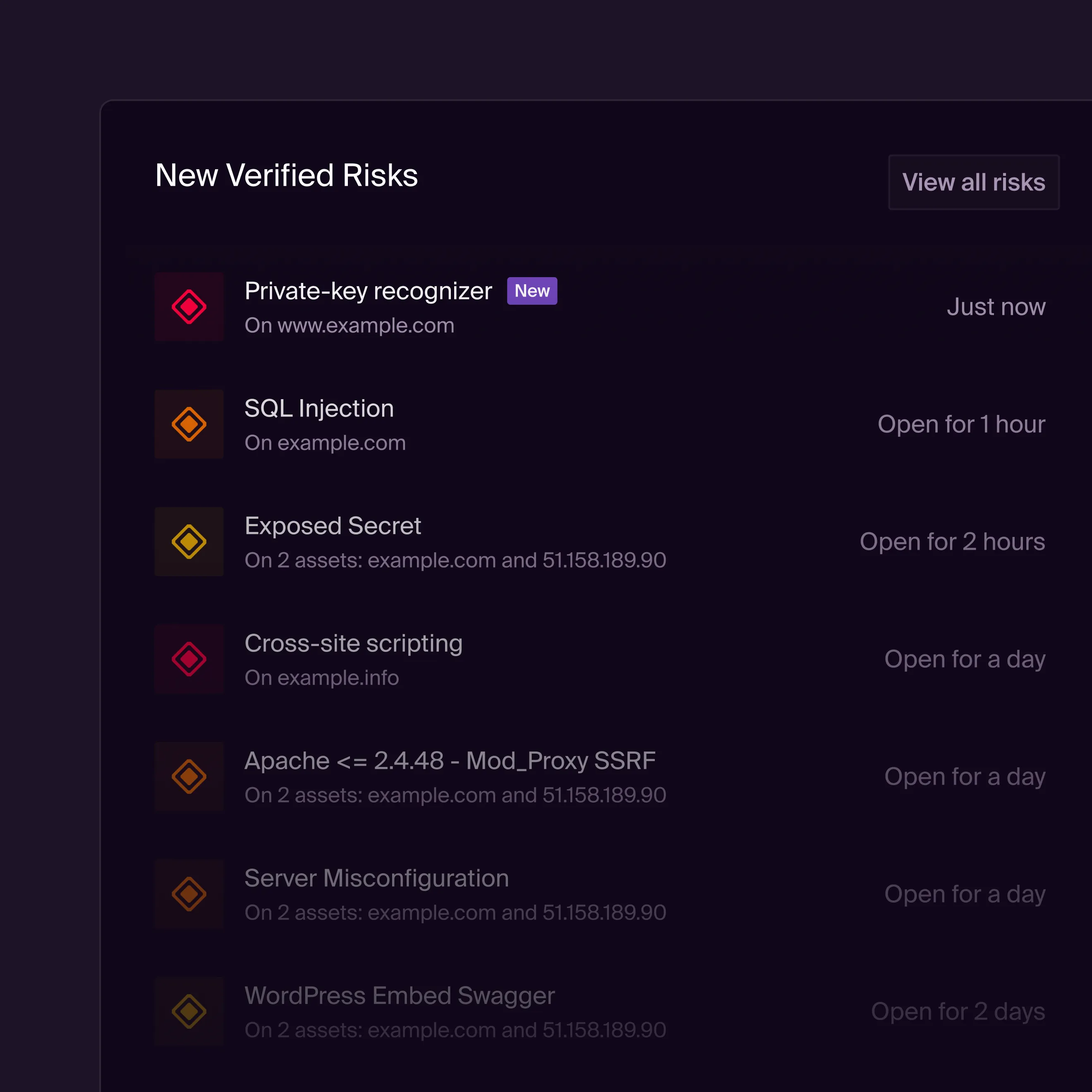
Agentic, autonomous, and immediate added value
AEV is delivered as a fully managed cloud service with no sensors to deploy, no agents to maintain. Onboard in minutes and start receiving actionable insights the same day. The autonomous engine continuously discovers, tests, and validates exposures without manual effort, so you gain enterprise‑grade adversary emulation without adding headcount or operational overhead.
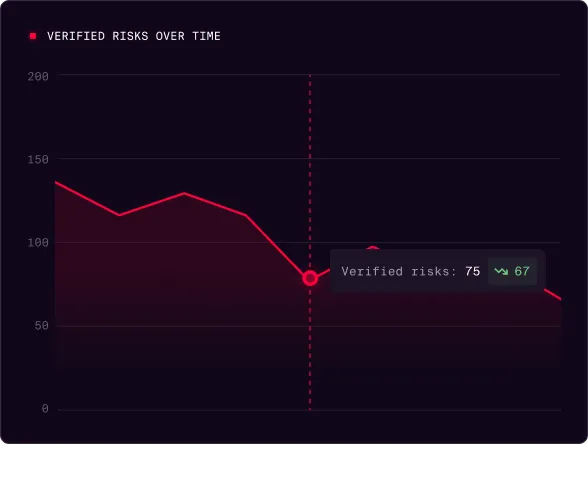
























Latest resources.
All resourcesTake the first step in the shoes of your adversary
Hadrian provides you with the hacker’s perspective on your internet-facing business to fortify your cybersecurity posture. Curious to know what they see?






.png)