Each year, thousands of cybersecurity professionals descend on Las Vegas for Black Hat. For nearly three decades, the conference has served as one of the most important global stages for the latest research, best practices, and toolsets. Because of its reputation and reach, Black Hat often shapes the direction of industry conversations for the months and years ahead.
At Black Hat 2025, the standout theme was agentic AI. Building on Gartner’s prediction that at least 15% of day-to-day work decisions will be made autonomously through agentic AI by 2028, this technology promises to radically change how security teams operate. But as with prior waves like continuous threat exposure management (CTEM) and Zero Trust, the question for CISOs is: what part of the agentic AI excitement reflects real innovation, and what is repackaged marketing jargon?
What is agentic AI and why the growing interest?
Agentic AI refers to autonomous systems capable of sensing, deciding, and acting independently to achieve goals within complex environments. Unlike traditional AI that supports humans by providing recommendations or data analysis, agentic AI agents operate with minimal human intervention, adapting and learning from their actions.
For example, traditional AI in security often acts as a co-pilot, by helping SOC analysts interpret data and support decision-making. In contrast, agentic AI functions more like an autonomous operator capable of independently detecting, managing, and responding to security risks without requiring direct prompts or continuous involvement from human analysts.
For CISOs struggling with staffing shortages, this difference is crucial. The ISC2 2024 Cybersecurity Workforce Study estimates a global shortfall of 4.8 million cybersecurity professionals, making it extremely challenging to build and maintain effective security teams. Agentic AI, which takes on a much more autonomous role than traditional AI, could maximize limited headcount, reduce alert fatigue, and maintain stronger security defenses even with smaller teams.
Agentic AI use cases highlighted at black hat
The agentic AI solutions on display at Black Hat showcased diverse and ambitious applications, pointing to where innovation is headed.
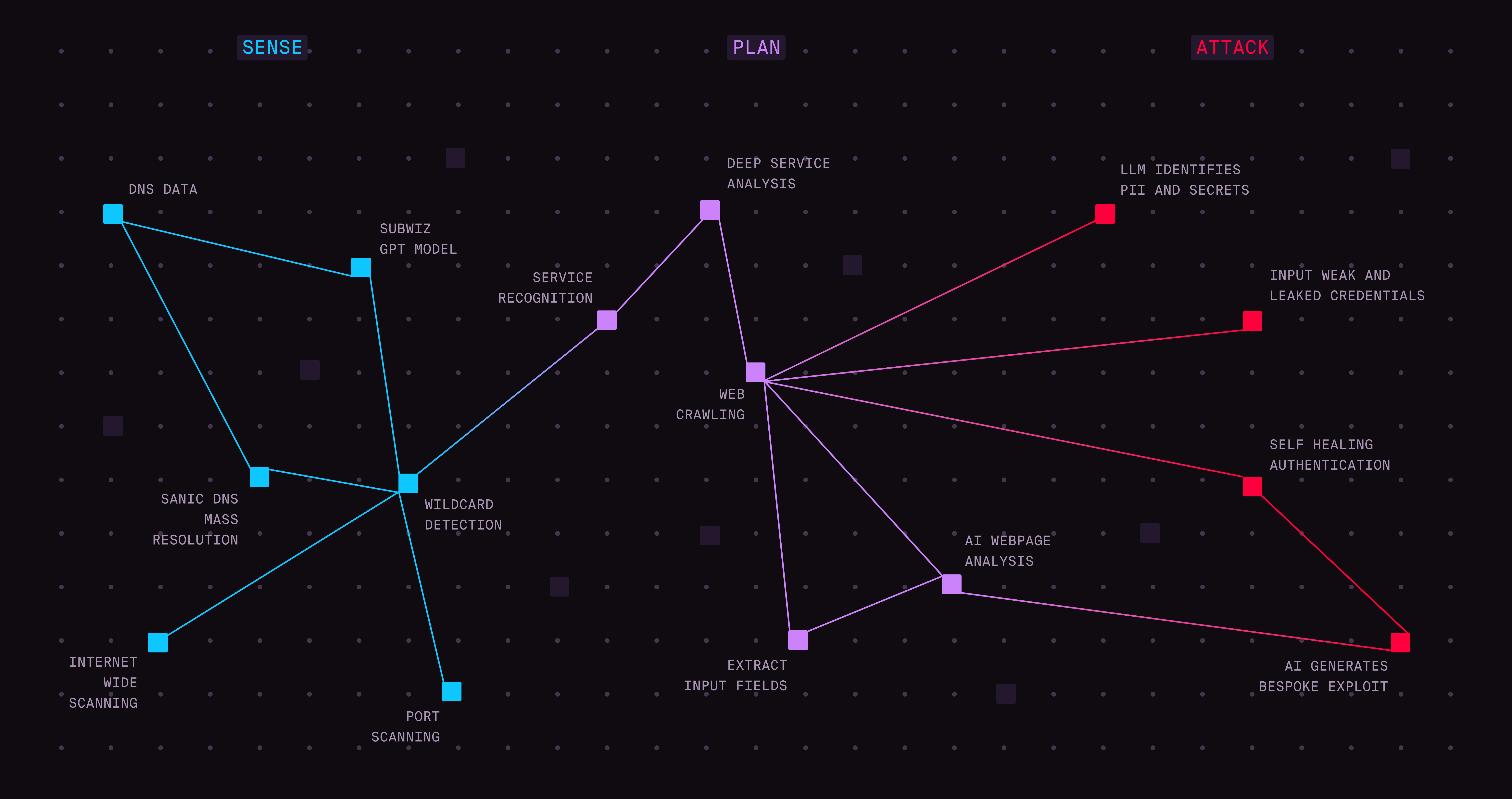
- Autonomous attack surface discovery and validation. Traditional attack surface management often relies on scheduled scans or static inventories that quickly become outdated. Agentic AI agents are being developed to operate continuously and autonomously, simulating attacker reconnaissance by exploring and probing digital assets in real time. This approach aims to identify previously unknown or hidden exposures, validate their exploitability, and prioritize them based on real-world impact. Future innovation in this space is focusing on improving context awareness, reducing false positives, and integrating remediation workflows to close the loop.
- Dynamic phishing and social engineering simulations. Static phishing simulations can quickly lose effectiveness as attackers evolve their techniques. Agentic AI is being applied to create adaptive phishing campaigns that autonomously craft, deploy, and refine attack scenarios based on user interactions and environment signals. By learning from recipient responses and adjusting tactics on the fly, these systems aim to enhance employee training and security readiness against increasingly sophisticated social engineering attacks. Next steps in this field include better modeling of attacker behavior and integrating human feedback loops to fine-tune campaigns.
- Automated incident response orchestration with autonomous decision-making. Incident response traditionally depends on human analysts triaging alerts and initiating containment measures, a process often slowed by alert fatigue and complexity. Agentic AI is being explored to autonomously detect exploitation attempts and orchestrate tailored containment workflows in real time. By applying contextual understanding and decision-making capabilities, these systems aim to reduce mean time to response and enable security teams to focus on strategic investigations. The future of this use case lies in enhanced explainability, cross-tool interoperability, and adaptive playbooks that evolve based on attack patterns.
These examples illustrate agentic AI’s potential to augment both offensive and defensive security operations, not by replacing humans, but by amplifying their effectiveness through autonomous, continuous, and context-aware action.
{{cta-automated-pentest}}
Navigating the agentic AI hype
Agentic AI’s rise mirrors earlier industry waves like CTEM and Zero Trust, which also generated excitement alongside confusion and marketing overuse when they made their splash at Black Hat in previous years. Many vendors rebrand existing solutions under new terminology, leaving CISOs to parse what truly represents a shift versus a repackaged product.
The challenge today is separating meaningful agentic AI innovation from buzzword-driven hype. CISOs need to critically evaluate claims, ask tough questions about autonomy, transparency, and integration, and resist pressure to adopt solutions based solely on trendiness. To navigate the agentic AI landscape, CISOs should focus on three practical actions that help differentiate substance from style.
Request clear demonstrations of autonomous capabilities.
Marketing materials frequently tout “autonomy” without clarifying what that means in practice. It’s vital to dig deeper. Ask vendors to show concrete examples where their agentic AI systems make independent decisions—such as identifying new exposures, choosing how to validate them, or dynamically adapting tests—without human intervention.
Beware solutions that primarily rely on automated workflows triggered by predefined scripts or static playbooks. Genuine agentic AI should operate with a level of goal-directed autonomy, such as mimicking attacker behaviors or response decisions, learning and adjusting as conditions evolve.
Question vendor claims critically
Agentic AI is often used as a catch-all term, sometimes masking existing capabilities repackaged under a trendier name. CISOs should challenge vendors to clearly explain how their offerings differ from traditional automation or earlier AI approaches.
Important questions include: What unique exposures can agentic AI identify that other tools miss? How does the system’s decision-making improve over time? Understanding these nuances helps avoid adopting solutions that deliver little beyond incremental automation.
Pilot with measurable outcomes
No amount of vendor promises replaces real-world validation. CISOs should begin with controlled pilots that focus on specific, measurable objectives such as uncovering previously unknown exposures, reducing false positive rates, or accelerating incident response times.
This approach enables security teams to assess agentic AI’s practical impact on their unique environments and workflows. Pilots also provide valuable data to inform scaling decisions and integration planning, reducing risk and building internal confidence in the technology’s value.
Hadrian’s agentic Offensive Security Platform
When evaluating agentic AI solutions, CISOs need clear demonstrations of autonomous capabilities that go beyond marketing buzzwords. Genuine agentic AI platforms make independent decisions, simulating attacker behavior autonomously and validating exposures in real-world conditions—not simply automating scripted workflows.
Hadrian’s Offensive Security Platform exemplifies this approach. Powered by agentic AI, it delivers continuous Adversarial Exposure Validation by actively probing exposures, prioritizing them based on true exploitability, and integrating remediation orchestration to help teams confidently accelerate fixes.
As Black Hat 2025 showed, agentic AI is moving from theory to practice, offering security teams unprecedented scale and precision to manage exposures proactively. However, CISOs must remain curious and skeptical, distinguishing real innovation from hype to make informed decisions. Hadrian remains committed to advancing agentic AI in ways that deliver measurable value and empower security teams to stay ahead in an increasingly complex cyber landscape.