Automated Penetration Testing
Discover the truly exploitable vulnerabilities and eliminate blind spots before attackers can strike with continuous, real-world attack testing.

























Real-time, event-driven testing
Hadrian’s Orchestrator AI runs security assessments the moment your attack surface changes, whether it’s a new asset, misconfiguration, or emerging exploit. Trained by elite ethical hackers, our platform mimics real adversary behavior to provide timely, targeted validation when it matters most.
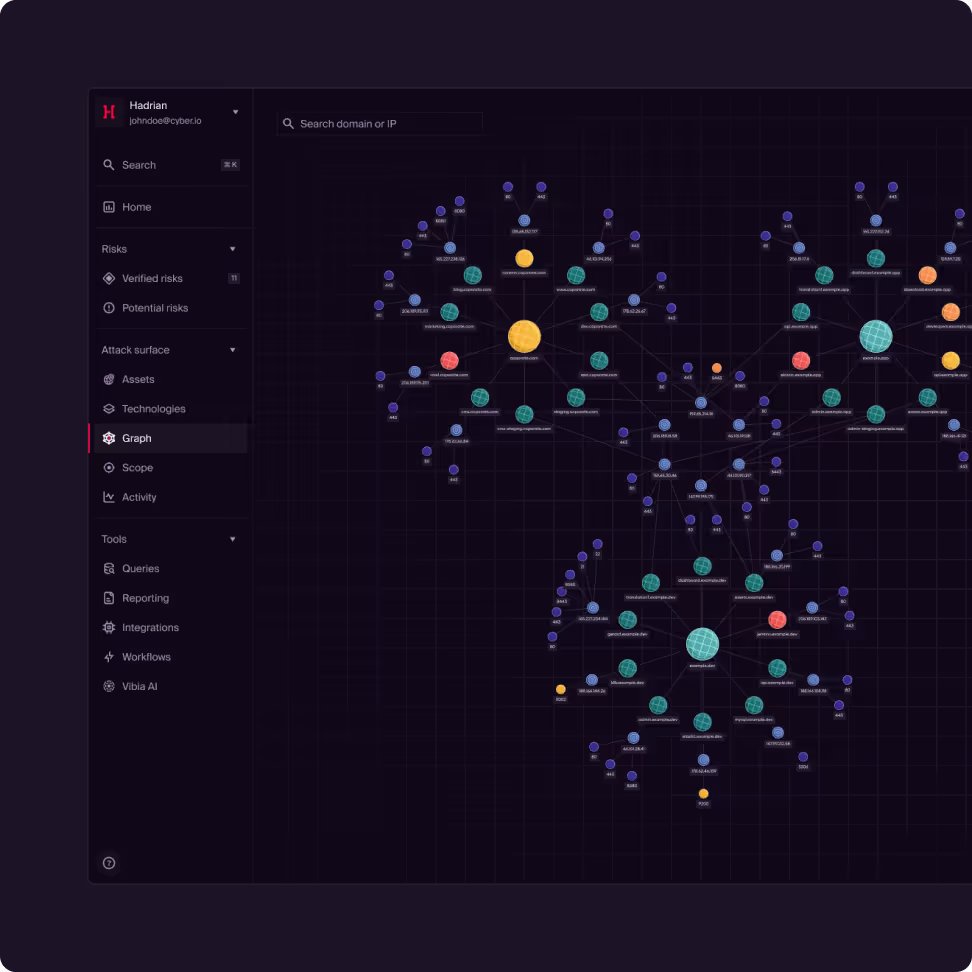
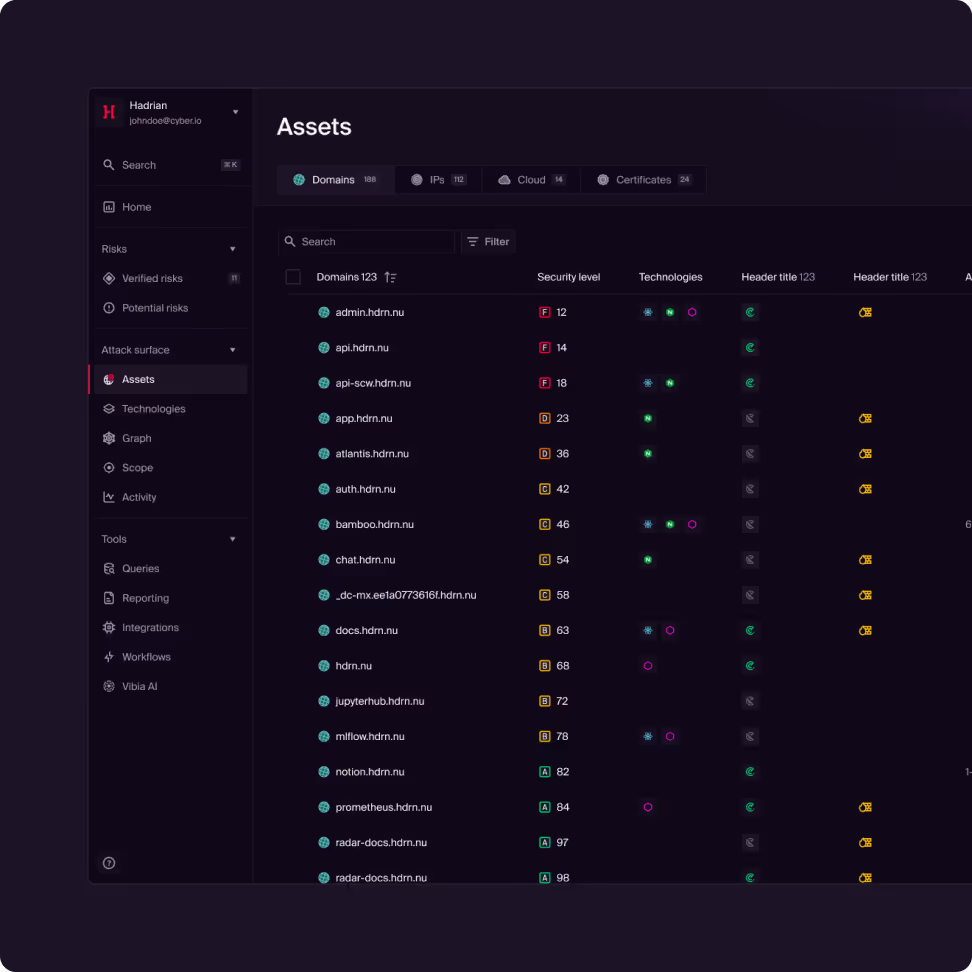
Test every asset. Zero blind spots.
Don’t just test your crown jewels; Hadrian continuously probes every asset, ensuring you see what attackers see before they see it. Hadrian provides 10x visibility of critical risks by testing every asset in the attack surface, preventing lateral movement from insecure infrastructure.
Validation that keeps you focused
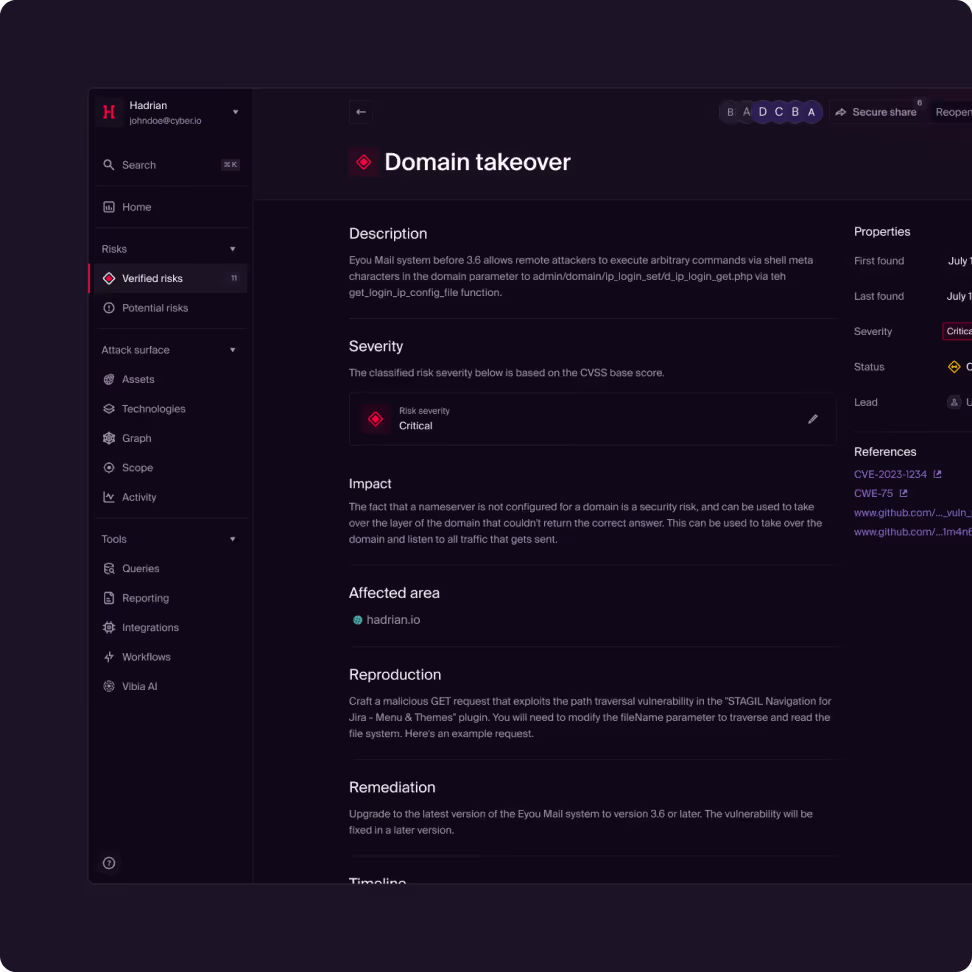
Forget the noise and boost remediation times by up to 80%. Hadrian cuts through false positives by replicating real-world exploitation paths, demonstrating exactly what attackers could do with each exposure. Powered by an AI-driven engine, every finding includes clear proof-of-exploit steps and contextualized risk prioritization–so you know where to focus first and respond faster.
Take the first step in the shoes of your adversary
Hadrian provides you with the hacker’s perspective on your internet-facing business to fortify your cybersecurity posture. Curious to know what they see?



























“It's not often that you find a tool that homes in on the risks that truly matter”
Mahdi Abdulrazak
Group Information Security & Risk Officer

“Event-driving testing saved time and energy with tests that leveraged insight”
Danny Attias
LBS Chief Digital & Information Officer
Frequently Asked
Questions
Cillum do magna irure labore et ea cupidatat ipsum nulla exercitation ullamco quis sunt proident.
Hadrian is an agentic AI offensive security platform that helps modern security teams prevent breaches before they begin. Agentic AI continuously discovers internet-facing assets, emulates attacker behavior, and validates which exposures are truly exploitable—cutting through noise and prioritizing what matters most. Hadrian delivers 10x visibility into critical risks, eliminates 99.4% of alert noise with reliable validation, and reduces remediation time by 80% with clear, reproduction-ready guidance.
Traditional scanners rely on static lists of known vulnerabilities (CVEs) and often produce a high volume of false positives. Hadrian goes beyond simple detection by performing Adversarial Exposure Validation. Our platform safely simulates real-world attack techniques to validate if a vulnerability is actually exploitable in your specific environment. This means we don't just tell you something might be wrong; we prove whether it matters.
We solve alert fatigue through validation. Most security tools flood teams with alerts based on theoretical severity (CVSS scores). Hadrian filters this noise by attempting to exploit the finding. If a vulnerability cannot be exploited due to a firewall or configuration, we deprioritize it. We only flag verified risks (true positives) that have a confirmed path to compromise, allowing your team to focus on what actually needs fixing.
Yes. One of our primary capabilities is autonomous asset discovery. We continuously scan the internet to find forgotten subdomains, cloud instances, and legacy servers that belong to your organization but aren't in your official inventory. You can’t protect what you can’t see, and Hadrian ensures you have 100% visibility over your external perimeter.
Experience Hadrian
Hadrian’s end-to-end offensive security platform sets up in minutes, operates autonomously, and provides easy-to-action insights.





.png)